Right now, the only jailbreakable iOS & iPadOS 14 devices at the time of this writing are those with the A9 and A9X chips, and though that could change in the near future as the checkra1n team works to supplement. Added support for A10 and A10X, but other devices are not vulnerable to the exploit of bootrom checkm8 error as before. However, well-known hacker and checkra1n team member Luca Todesco shared a particularly interesting announcement via Twitter yesterday afternoon that he exploited a bug on iOS 14.0.1 to jailbreak and be able to do. show PAC bypass (an important step for more hijacking on iOS systems).
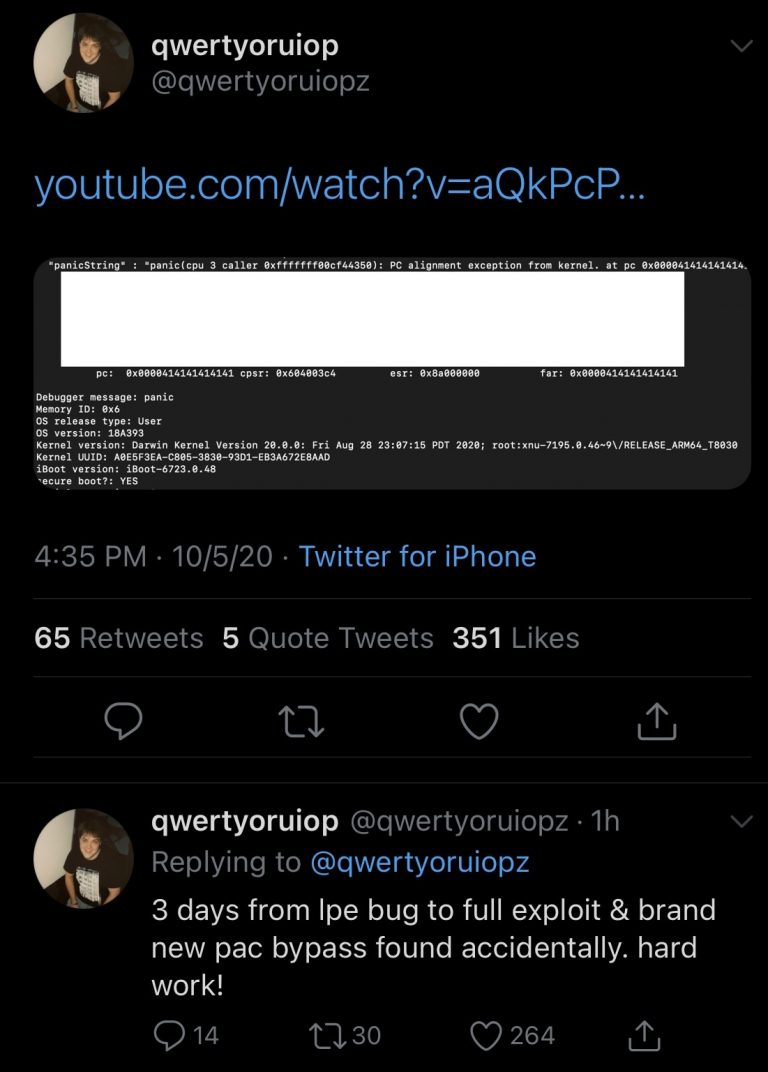
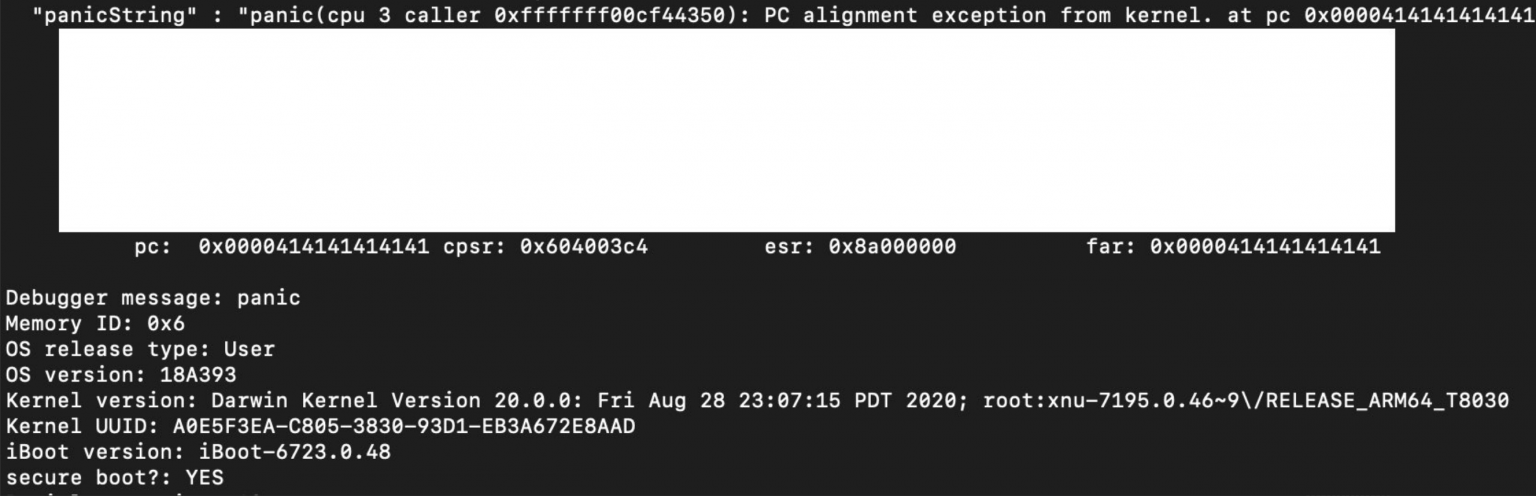
Luca Todesco said it took him only three days to move from a local override (LPE) bug to a full-blown exploit and get past the PAC mechanism. This error was discovered by accident. A screenshot shared by Todesco shows the device he is running on an A13 chip with iOS 14.0 .1 (build 18A393) – the latest version of iOS and iPadOS as of now.
It is not clear from the details posted above whether Todesco will release this new exploit to the community. Before that Luca once released the yalu jailbreak tool. Or recently, this hacker was involved in the bootrom-based jailbreak checkra1n.
With the aforementioned cases, one of three things can happen: 1) Todesco can keep the mining itself for research purposes; 2), Todesco can provide this error to the Oydssey and un0ver team to combine; 3) Todesco can use this exploit to create its own jailbreak.
In any case, this is great news for the jailbreak community as there are several other exploits released for iOS & iPadOS 14 that are likely to pave the way for future jailbreaks for the latest mobile operating systems. and best of Apple.





Post a Comment
Post a Comment